Configure DNSSEC with BIND
The DNS plays a critical role in supporting the Internet infrastructure by providing a distributed and fairly robust mechanism that resolves Internet host names into IP addresses and IP addresses back into host names. The DNS also supports other Internet directory-like lookup capabilities to retrieve information pertaining to DNS Name Servers, Canonical Names, Mail Exchangers, etc. Beeing almost 30 years old, it started to show its age. The threats that surround the DNS are due in part to the lack of authenticity and integrity checking of the data held within the DNS and in part to other protocols that use host names as an access control mechanism. The most common types of DNS attacks are:
- DNS Spoofing (also known as DNS Cache Poisoning)
- Malicious Resolvers
- Man-in-the-middle (MITM)
DNSSEC was designed to protect Internet resolvers (clients) from forged DNS data, such as that created by DNS cache poisoning. It is a set of extensions to DNS, which provides to DNS clients (resolvers):
- Origin authentication and data integrity: DNSSEC-capable resolvers are able to digitally verify that the DNS data they receive is identical to the information on the authoritative DNSSEC-capable name server. This is done by authenticating the origin and integrity of DNS data as it transits the Internet.
- Authenticated denial of existence: DNSSEC-capable resolvers are able to determine whether or not a resource, such as a name server, actually exists.
To activate DNSSEC you'll need three things:
- gTLD/cTLD (gloabal/country Top-Level-Domain) support for DNSSEC.
- The register should accept DS Records (Delegation Signor) and send them to Top-Level-Domain (TLD) for your domain.
- The authoritative name server support for DNSSEC to (re)sign your DNS zone.
Since an example is like a thousand words, i'll use the following:
- .net as a gTLD which has DNSSEC support already.
- Duiadns.net as a domain whos register has DNSSEC support already (see the picture below):
- Bind as an authoritative name server configured like this:
Activate DNSSEC in /etc/named.conf:
options {
dnssec-enable yes;
dnssec-validation yes;
dnssec-lookaside auto;
}
Before creating ZSK(Zone Signing Key) si KSK(Key Signing Key) please install haveged. Without it, you'll have to wait couple of minutes for those two keys to generate. Create a directory to store the keys:
mkdir /etc/pki/dnssec-keys/
Generate ZSK(Zone Signing Key):
cd /etc/pki/dnssec-keys/ dnssec-keygen -f KSK -a NSEC3RSASHA1 -b 4096 -n ZONE duiadns.net
Now there are four keys (2 public/private pairs for ZSK si KSK) in /etc/pki/dnssec-keys/:
[xxx]# ls -la *Kduiadns.net*
07:30 Kduiadns.net.+007+16940.key
07:30 Kduiadns.net.+007+16940.private
07:30 Kduiadns.net.+007+50703.key
07:30 Kduiadns.net.+007+50703.private
Add the keys in duiadns.net.db zone file:
cd /etc/pki/dnssec-keys/
for key in `ls Kduiadns.net*.key`
do
echo "\$INCLUDE /etc/pki/dnssec-keys/$key">> /var/name/master/duiadns.net.db
done
Sign duiadns.net zone:
cd /var/name/master/
dnssec-signzone -S -K /etc/pki/dnssec-keys -e +3024000 -o duiadns.net -N INCREMENT duiadns.net.db
duiadns.net.db.signed file should be generated. Add it to /etc/named.conf replacing duiadns.net.db:
zone "duiadns.net" in {
type master;
file "/var/named/master/duiadns.net.db.signed";
..............
}
I suggest to operate only duiadns.net.db file in the future and re-generate duiadns.net.db.signed every time you make a change using the following script:
./dnssec-sign-zone.sh duiadns.net
[xxx]# cat dnssec-sign-zone.sh
#!/bin/sh
PDIR=`pwd`
SIGNZONE="/sbin/dnssec-signzone"
DNSSEC_KEYS="/etc/pki/dnssec-keys"
ZONEDIR="/var/named/master"
ZONE=$1
cd $ZONEDIR
SERIAL=`/usr/sbin/named-checkzone $ZONE $ZONE.db | egrep -ho '[0-9]{10}'`
sed -i 's/'$SERIAL'/'$(($SERIAL+1))'/' $ZONE.db
$SIGNZONE -S -K $DNSSEC_KEYS -e +3024000 -o $ZONE -N INCREMENT $ZONE.db
systemctl restart named
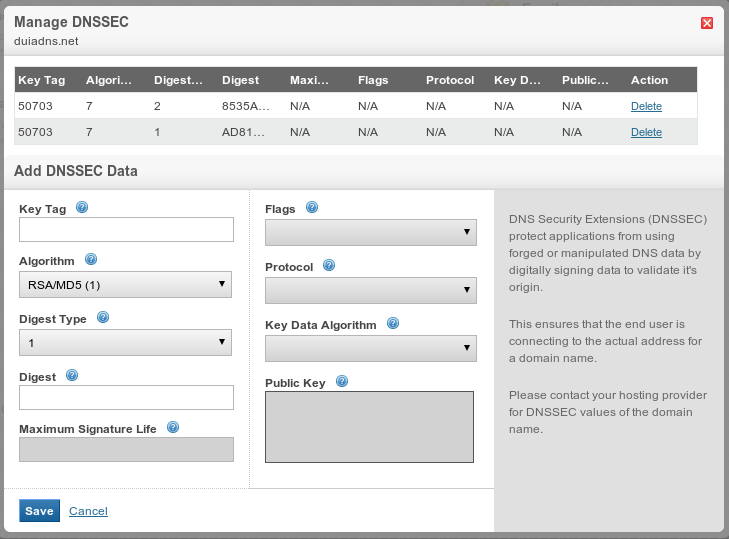
Let's go back to step 2 because now a file called dsset-duiadns.net. was generated and it contains all the info we need to make DS Records i've mentioned above.
[xxx]# cat dsset-duiadns.net.
duiadns.net. IN DS 50703 7 1 AD819997BE5847844F55B70987F9BA1630DCD682
duiadns.net. IN DS 50703 7 2 8535A8C0EC3638F72DA84C87C65D4AF2F2624D8184159E516E3C3FBA D3018065
On the Register's webpage, complete the form (see the image below) with data from dsset-duiadns.net. file:Restart DNS daemon (bind/named) and you're all set.
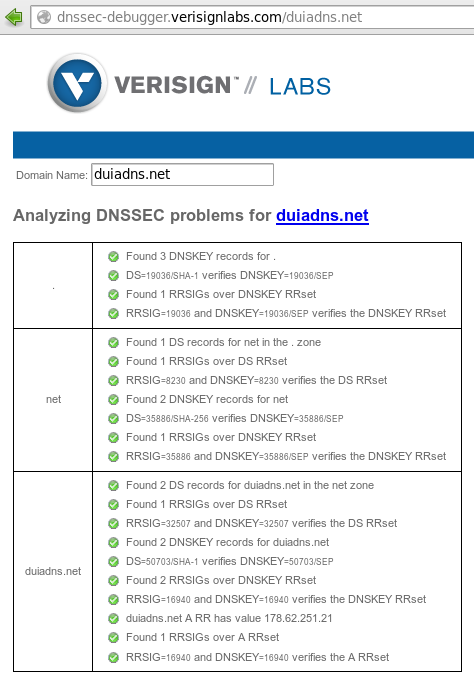
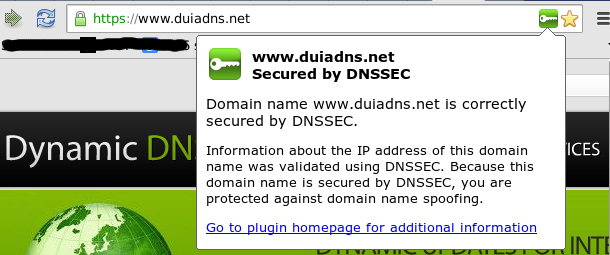
To check if a domain is DNSSEC signed you could use dnssec-debugger.verisignlabs.com website: or simply install an addon for your browser.
Config Tutorials
Recent Comments
Contente Publisher on Telegram Notification
Contente Publisher on Telegram Notification
Slaveanu Ionut on Running Duiadns on Apple Router
tim lensen on Running Duiadns on Apple Router
tim lensen on Running Duiadns on Apple Router
Slaveanu Ionut on Running Duiadns on Apple Router
Gleb Miller on Running Duiadns on Apple Router

Leave a Comment